While the networking side of our operation is fairly simple (actually mimics a routing small business setup), there are a couple gotchas that I ran into that one would not expect. The components of our network setup include:
- HP Procurve 1800-24G – this connects all of the machines together, both on the storage and management side of things. Yes it’s old school, but switches have not evolved terribly in the small business sector, and this switch will definitely suit the home.lab project.
- Juniper SSG5 – this is our firewall to keep the villains out of the DMZ (our servers exposed to the publix) as best possible. Similar to the above, the SRX line is the current standard for Juniper (like the ASA for Cisco) on the small business line, but the SSG is pretty cheap on eBay, and has a ton of functionality. If you can figure out the SSG5 to its fullest potential, you’ll have no problems getting pro networking jobs.
- Verizon FiOS router – this is the final hop to the internet. If you are keeping your server network on the same subnet as your workstations (i.e. no SSG5 or other firewall in your config), this portion of the config is not necessary. For any production use, however, I strongly recommend a hardware firewall. The Verizon has decent firewall settings (including NAT and PAT) but I personally like a second layer of protection when possible.
HP Procurve Switch Setup
The most important steps on our managed switch will be to setup the proper LAG/LACP groups, create a second VLAN for the storage subnet, and enable SNMP so we can monitor all the ports and bandwidth in Cacti.
Juniper SSG-5
On the Juniper side, we have to create a DMZ subnet (which comes standard with the device), as well as a Trust VLAN for the workstations, so they are isolated from both the DMZ and the outside world. The Trust VLAN will have access to the DMZ and Untrust locations, but not the other way around. This is done with policies with Juniper, which I will go into further detail on it’s own page.
Verizon FIOS MI424 Router
A fairly standard issue home router, does the basic NAT translation and has built-in wifi access. This device can actually do a decent amount of firewalling if you are tight on funds for a separate firewall for your DMZ network.
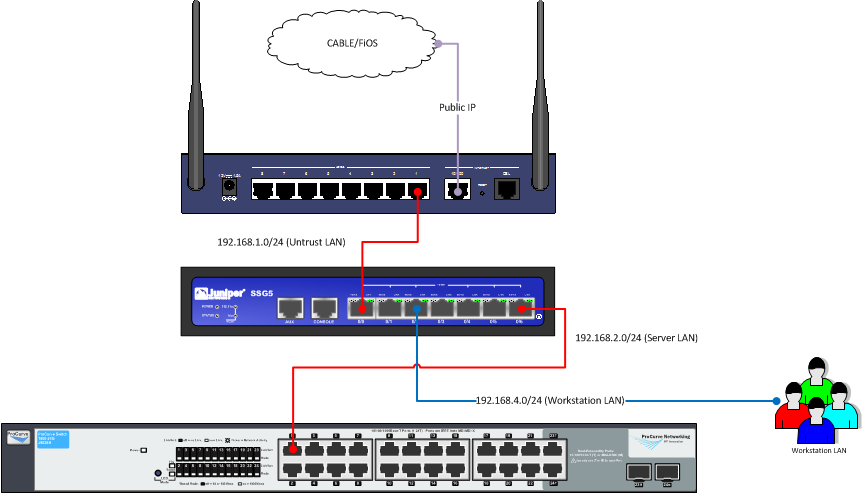
Network Diagram
It’s easier to look at the network, even though it is a simple setup, as a logical setup, as well as the hypervisor network setup (which requires its own degree of networking). The logical setup, including our cablemodem, firewall, and networking switch is below:
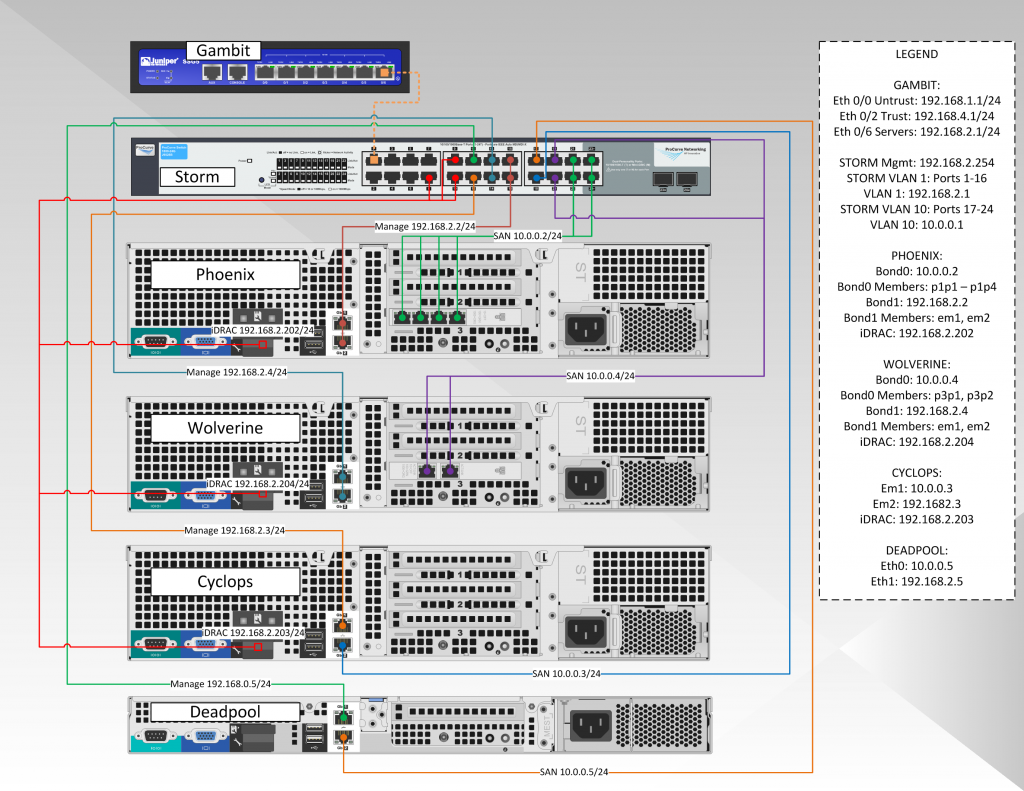
The Hypervisor network has a few more moving parts. While it can look a little confusing and give the appearance of a complicated setup, it is not. From a big picture perspective, yes there are a lot of moving parts, but if you take each step one at a time, it’s pretty straightforward:
We’ll break down each server and the entire network step in their own pages. The HP switch believe it or not is pretty easy to setup. The SSG5 is a little tougher than it looks, especially if you want to get the proper security. And by tougher, I mean you have to fine tune the configuration, not that configuration is difficult. Some of the tweaks require trial and error, which of course burns some spare time.